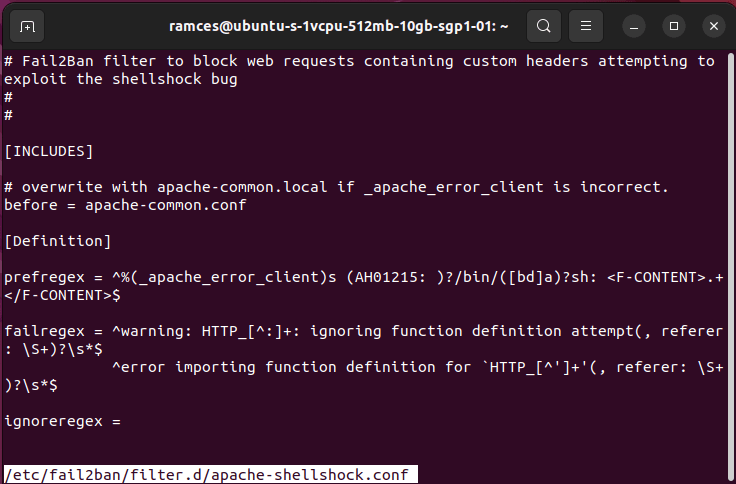
Fail2Ban comes with many built-in filters for common services like SSH, Apache, and Postfix. But for custom applications, web apps (e.g., WordPress login attempts), or specific log patterns, you’ll need to create your own filters. This allows Fail2Ban to detect unique failure patterns and ban offending IPs automatically.
Continue reading Custom Fail2Ban Filters: A Step-by-Step TutorialTag: Guide
Nginx Proxy Manager Docker Setup Guide
In today’s self-hosting world, managing multiple web services (like Nextcloud, Plex, or Home Assistant) can quickly lead to a “port-forwarding nightmare.” Nginx Proxy Manager (NPM) is the ultimate solution, providing a clean web interface to manage reverse proxies and SSL certificates without touching a single line of Nginx configuration files.
Continue reading Nginx Proxy Manager Docker Setup GuideBeginner’s Guide to iostat
Ever wondered what’s going on “under the hood” of your Linux system when things feel a bit slow? While CPU and memory are often the first things we check, disk input/output (I/O) can be a major bottleneck. That’s where the iostat command comes in – a powerful yet often overlooked tool for understanding how your storage devices are performing.